MunishKumar G
Founder & CEO - BugDiscover, Offensive Security Expert, Red Teaming and Information Security Consultant.
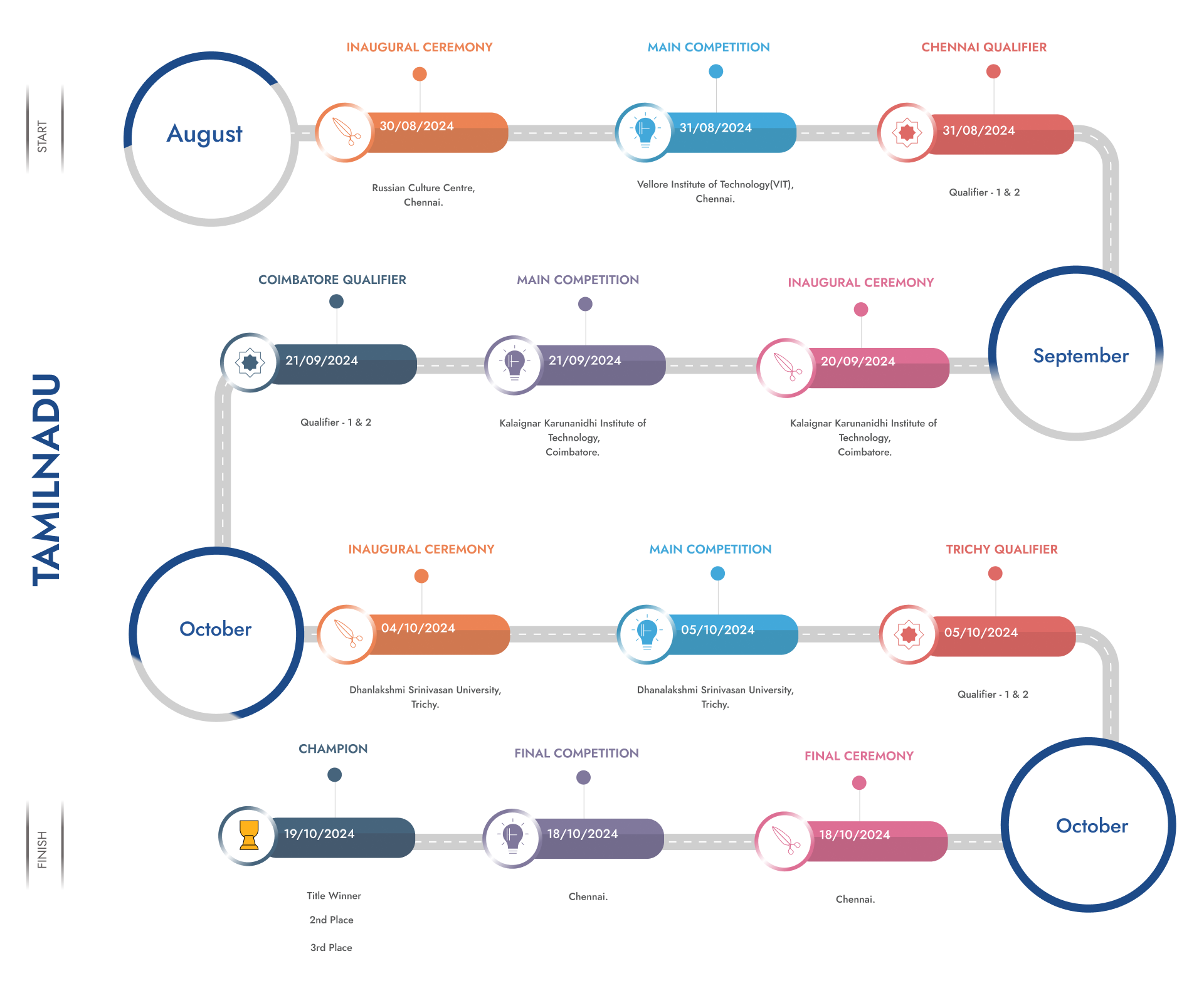
30th and 31st August, 2024.
Russian Culture Centre, Chennai 18
Hackathon X: India's Largest and Most Prestigious Cybersecurity Competition. Here's a list of potential participants:
Founder & CEO - BugDiscover, Offensive Security Expert, Red Teaming and Information Security Consultant.
Country Head - India, Primoris Systems LLC, Vice President - Hexaforce Solutions, Technical Head - NCSRC, New Delhi.
Global Head of Cyber Risk & Data Privacy - BFSI R&C @ TCS
Global Head - Cybersecurity (Manufacturing, Supply Chain & Retail), Dyson.











